Our engineers conduct security risk assessments to help you identify key focus areas for building cybersecurity resilience. By providing a roadmap of prioritized action plans, Optic empowers you to make strategic improvements to support business and compliance goals.
With decades of experience performing cybersecurity risk assessments, Optic’s team of cybersecurity engineers developed our Know Your Risk process to perform assessments for organizations based on their specific risks and requirements to ensure meaningful results. From a small subset of systems, to an entire cybersecurity program, we have worked with organizations across industries to conduct assessments, providing visibility into their core capabilities. Our core assessment services include Cybersecurity Framework Assessments, Cybermaturity Assessments, Penetration & Vulnerability Assessment, and Supply Chain Assessments, further defined below.
Using our deep knowledge and experience of cybersecurity principles, we are also able to support a multitude of additional assessments against regulatory requirements, standards, and frameworks including: ISO/IEC 27001, NIST Risk Management Framework (RMF), HIPAA, NIST Privacy Framework, California Consumer Privacy Act (CCPA), Cybersecurity Maturity Model Certification (CMMC), and security controls catalogues including NIST SP 800-53.

Our engagements go beyond simply providing a listing of findings. We create tailored, risk-informed roadmaps aligned with business and compliance goals to drive improvements across your cybersecurity program.
For more information about Optic Cyber Solutions and our services, send us an email at Info@OpticCyber.com.
Cybersecurity risks are on the rise as threat actors continually become more sophisticated. Simply deploying more advanced security technologies without having a firm understanding of your cybersecurity program’s core competencies may lead to only a nominal reduction to your risk exposure.
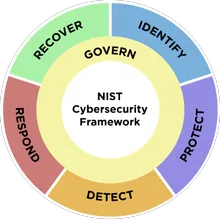
Utilizing Optic’s Know Your Risk process, our cybersecurity assessments are approached from a risk-based perspective and utilize the NIST Framework for Improving Critical Infrastructure Cybersecurity (NIST Cybersecurity Framework), which established a common language for describing a cybersecurity program in terms of identifying, protecting, detecting, responding, and recovering from threats. By using the Cybersecurity Framework, we can perform a comprehensive assessment of the current state of your cybersecurity program, develop a risk-informed target state identifying areas to improve, and provide action plans to successfully reach your target state goals.
| Maturity
As cybersecurity is implemented, a method for measuring and understanding your capabilities is essential. Our engineers have worked directly with the CMMI Institute to develop the cybersecurity content behind their Cybermaturity Platform (CMMI-CP) and supported many organizations in the United States Defense Industrial Base (DIB) as they begin preparing for a Cybersecurity Maturity Model Certification (CMMC).
Leveraging this experience, we assist organizations large and small in conducting CMMI Cybermaturity Assessments and CMMC Readiness Assessments.
Through both assessments, our team of experts will determine the current maturity of a cybersecurity program and identify the greatest cybersecurity risks. By understanding the business risks of an organization, along with the current baseline maturity, we develop roadmaps for improvement to close gaps while moving toward a targeted maturity level consistent with your business and regulatory requirements. If you need help understanding where you are today and what to do next reach out at Info@OpticCyber.com.
| Penetration & Vulnerability
For organizations wanting a targeted assessment of their technical security controls, we offer vulnerability assessment and penetration testing services to identify and exploit gaps missed by typical vulnerability scans. We customize each penetration test based on client needs and focus on identifying weaknesses in the systems being tested to identify flaws and insecure implementations.
In addition to identifying and categorizing specific findings based on criticality, we provide actionable recommendations including security architecture improvements that will bolster the overall security program. Our approach ensures that the root cause the vulnerabilities are resolved and not just the findings.
| Supply Chain
The introduction of risks via the supply chain is a growing problem that impacts the security of many organizations across sectors. Organizations never want to be caught off guard in the event of a data breach by one of their vendors.
Our engineers worked with the team that developed the NIST SP 800-161, “Supply Chain Risk Management Practices for Federal Information Systems and Organizations” which incorporates best practices for identifying and assessing supply chain risk from experts across industry. Our cybersecurity engineers leverage this expert knowledge to assist you in managing the risk imposed by vendors by assessing key aspects of your cybersecurity program without requiring an extensive audit. This approach allows for faster risk-informed decision making and provides input for refining your organization’s vendor risk management program.